Cloud Infrastructure Entitlement Management Market 2030: CyberArk’s Game-Changing Acquisition of C3M
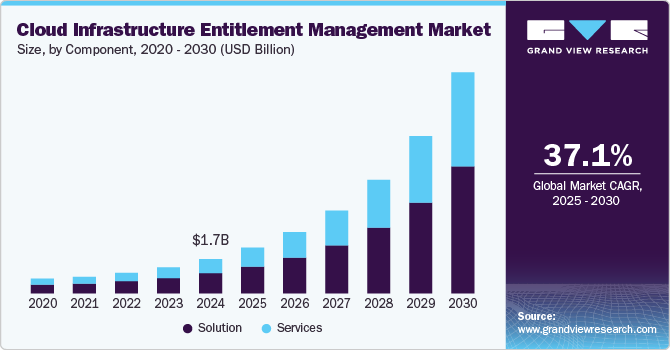
A security revolution is unfolding in the cloud! The global cloud infrastructure entitlement management (CIEM) market was an estimated USD 1.68 billion in 2024 and is poised for an astonishing surge, projected to grow at a blistering CAGR of 37.1% from 2025 to 2030.
A security revolution is unfolding in the cloud! The global cloud infrastructure entitlement management (CIEM) market was an estimated USD 1.68 billion in 2024 and is poised for an astonishing surge, projected to grow at a blistering CAGR of 37.1% from 2025 to 2030. This isn't just another tech trend; it's an essential evolution within cloud security, meticulously focused on managing, monitoring, and safeguarding all those crucial cloud-based permissions and entitlements. As organizations increasingly venture into the complex landscapes of multi-cloud and hybrid cloud environments, ensuring proper access control management has become a top-tier security imperative. CIEM solutions are the unsung heroes here, empowering businesses to rigorously enforce the principle of least privilege (PoLP) – guaranteeing that users and applications possess only the precise permissions they need, thereby drastically slashing the risk of unauthorized access and insidious insider threats.
The demand for CIEM solutions is rocketing, driven by the sheer complexity of today's cloud environments where traditional Identity and Access Management (IAM) solutions simply can't keep pace with the need for fine-grained permissions. CIEM dives deeper, offering unparalleled visibility, robust automation, and powerful remediation capabilities to address misconfigurations and excessive entitlements that often slip through the cracks. With global cloud adoption accelerating at an unprecedented rate, the CIEM market is gaining strong traction across diverse industries, from banking and healthcare to retail, IT, government, and manufacturing. It's a challenging world where organizations juggle multiple cloud service providers like AWS, Microsoft Azure, and Google Cloud, each with its own distinct access management frameworks. This patchwork creates a nightmare for consistently securing and managing entitlements. Here's where CIEM shines, providing a centralized view, automated policy enforcement, and risk-based entitlement management across the entire cloud infrastructure. These solutions are pivotal in detecting overprivileged permissions, preventing unauthorized access, and ensuring strict compliance with security regulations. As cloud adoption continues its relentless march, the need for robust entitlement governance becomes paramount, solidifying CIEM's role as a crucial component of modern cloud security architectures and a key engine of market expansion.
Get a preview of the latest developments in the Cloud Infrastructure Entitlement Management Market; Download your FREE sample PDF copy today and explore key data and trends
Looking ahead, the market is set for truly significant expansion, propelled by heightened awareness, evolving regulatory requirements, and exciting advancements in automation, AI-driven security analytics, and the adoption of zero-trust frameworks. A major trend shaping the market is the seamless integration of CIEM with broader cloud security platforms. Leading vendors are ingeniously incorporating machine learning, sophisticated behavior analytics, and real-time risk assessment into their CIEM offerings. This empowers organizations to proactively detect and mitigate entitlement-related risks before they become critical. The intelligent application of AI and automation will dramatically enhance security teams' ability to identify anomalous permissions, privilege escalations, and compliance violations with unprecedented efficiency.
However, despite its critical importance, a significant hurdle for the CIEM market is the persistent lack of awareness and understanding among many enterprises regarding its absolute necessity. A considerable number of businesses still cling to traditional Identity and Access Management (IAM) and Cloud Security Posture Management (CSPM) tools, mistakenly believing they offer sufficient control over cloud permissions. Yet, these conventional solutions fundamentally lack the granular entitlement visibility and automated least privilege enforcement that CIEM specifically provides. Without a proper grasp of CIEM's profound benefits in mitigating excessive permissions and misconfigurations, organizations remain dangerously vulnerable to security breaches. Therefore, educating enterprises about CIEM's indispensable role in comprehensive cloud security is not just important – it's crucial for achieving broader market adoption.
Detailed Segmentation
Component Insights
The solution segment accounted for a market share of over 58% in 2024. The adoption of zero trust architecture (ZTA) is a major driver for CIEM solutions, as organizations move away from perimeter-based security to continuous identity verification. Zero Trust requires strict access controls, least privilege enforcement, and real-time monitoring of cloud entitlements. CIEM solutions support this model by identifying excessive permissions, enforcing just-in-time (JIT) access, and detecting anomalous entitlement behaviors. They help mitigate insider threats, privilege escalation, and unauthorized access by ensuring that users and applications have only the permissions they need at any given time. This proactive security approach strengthens cloud environments against evolving cyber threats while ensuring compliance with security policies.
Organization Size Insights
The large enterprises segment accounted for the largest market share in 2024. With the rise in cyber threats, insider attacks, and regulatory pressures, large enterprises are shifting from reactive to proactive cloud security strategies. Traditional Identity and Access Management (IAM) and Cloud Security Posture Management (CSPM) tools often fail to detect excessive entitlements and misconfigurations in real time. Cloud Infrastructure Entitlement Management (CIEM) solutions provide continuous monitoring, automated entitlement governance, and real-time threat detection, ensuring least privilege access and rapid remediation of security risks. By leveraging AI-driven anomaly detection and automated access controls, CIEM enables enterprises to prevent privilege escalation, enforce Zero Trust principles, and strengthen cloud security posture, reducing the risk of data breaches and compliance violations.
End-use Insights
The BFSI segment accounted for the largest market share of over 20% in 2024. BFSI companies are increasingly moving to cloud environments to benefit from scalability, cost savings, and operational efficiency. However, with the growing adoption of multi-cloud and hybrid cloud infrastructures, managing entitlements and identities becomes more complex. Misconfigurations or improper access controls can lead to security vulnerabilities, exposing sensitive financial data. CIEM solutions offer a centralized management approach, enabling organizations to monitor and govern access permissions across diverse cloud platforms. This ensures that only authorized users have the necessary access, reducing the risk of cloud security misconfigurations and enhancing the overall security posture of BFSI organizations in cloud environments.
Regional Insights
North America cloud infrastructure entitlement management market held the significant share of over 37% of the in 2024. North American companies are embracing digital transformation to enhance operational efficiency, improve customer experiences, and drive innovation. As organizations shift to cloud-first strategies, the complexity of managing access governance grows. Cloud Infrastructure Entitlement Management (CIEM) solutions become crucial in this context by enabling secure cloud adoption, ensuring proper access control, and minimizing security risks. CIEM solutions help organizations manage entitlements and identities across diverse cloud environments, supporting digital transformation while maintaining strong cloud security and compliance.
Key Cloud Infrastructure Entitlement Management Companies:
The following are the leading companies in the cloud infrastructure entitlement management market. These companies collectively hold the largest market share and dictate industry trends.
- Microsoft Corporation
- CyberArk
- Palo Alto Networks
- Check Point Software Technologies Ltd
- Zscaler, Inc.
- BeyondTrust Corporation
- Rapid7
- CrowdStrike
- SailPoint Technologies, Inc
- Saviynt Inc.
- Orca Security
- NextLabs
Cloud Infrastructure Entitlement Management Market Segmentation
Grand View Research has segmented the global cloud infrastructure entitlement management (CIEM) market report based on component, organization size, end-use, and region:
- Component Outlook (Revenue, USD Million, 2018 - 2030)
- Solution
- Services
- Organization Size Outlook (Revenue, USD Million, 2018 - 2030)
- Small and Medium-sized Enterprises (SMEs)
- Large Enterprises
- End-use Revenue, USD Million, 2018 - 2030)
- BFSI
- Healthcare & Life Sciences
- Retail & E-Commerce
- Government & Defense
- Manufacturing
- IT and ITeS
- Others
- Regional Outlook (Revenue, USD Million, 2018 - 2030)
- North America
- U.S.
- Canada
- Mexico
- Europe
- Germany
- UK
- France
- Asia Pacific
- China
- India
- Japan
- South Korea
- Australia
- Latin America
- Brazil
- Middle East & Africa
- U.A.E
- Saudi Arabia
- South Africa
- North America
Curious about the Cloud Infrastructure Entitlement Management Market? Download your FREE sample copy now and get a sneak peek into the latest insights and trends
Recent Developments
- In April 2023, Orca Security introduced Orca CIEM to secure identities and entitlements across multi-cloud environments. It provides visibility, risk detection, and automated remediation for excessive permissions and misconfigurations. By integrating CIEM with its cloud security platform, Orca helps organizations enforce least-privilege access, reducing cloud security risks and strengthening overall identity governance.
- In June 2022, Microsoft introduced Microsoft Entra, a suite of identity and access management solutions, to enhance secure access in hybrid and multi-cloud environments. Entra includes Azure Active Directory (AD), Cloud Infrastructure Entitlement Management (CIEM), and Decentralized Identity solutions. It helps organizations manage permissions, identities, and security risks, aligning with Zero Trust principles. This launch strengthens Microsoft’s commitment to secure digital transformation across enterprises globally.
- In August 2022, CyberArk, acquired cloud security specialist C3M to strengthen its Cloud Infrastructure Entitlement Management (CIEM) capabilities. This acquisition enhances CyberArk’s ability to provide automated access governance, privilege control, and compliance enforcement across multi-cloud environments. By integrating C3M’s expertise, CyberArk aims to help enterprises reduce cloud security risks, prevent overprivileged access, and adopt Zero Trust principles more effectively.